Previously we observed the process of installation of the free SSL certificate on Ubuntu 22.04, Ubuntu 18.04, and Ubuntu 16.04. In this post, you will learn how to install or renew the SSL certificate by Comodo on AWS EC2 instance or any Linux server.
Purchase and Install SSL certificate
Step 1 - Purchase SSL certificate
Choose SSL type
In order to purchase Comodo Positive SSL certificate, please execute the following steps:
- Go to the SSL Shopping Cart
- proceed with the best option that suits you.
Our partners provide our customers with several options at cheap prices:
- Positive SSL certificate with a one-year subscription
- Positive SSL certificate with two years subscription
- Positive SSL wildcard certificate
It is up to you which option to select. If you need a regular and common choice as your AWS SSL certificate EC2 - choose Positive SSL. If you need SSL for multiple subdomains you will have to use wildcard SSL.
SSL configuration
As soon as you made and paid for your order you will be able to Generate CRS.
Please fill in corespondent fields in the CRS generator and pay attention to Common Name - this is your domain name where SSL certificate will be installed.
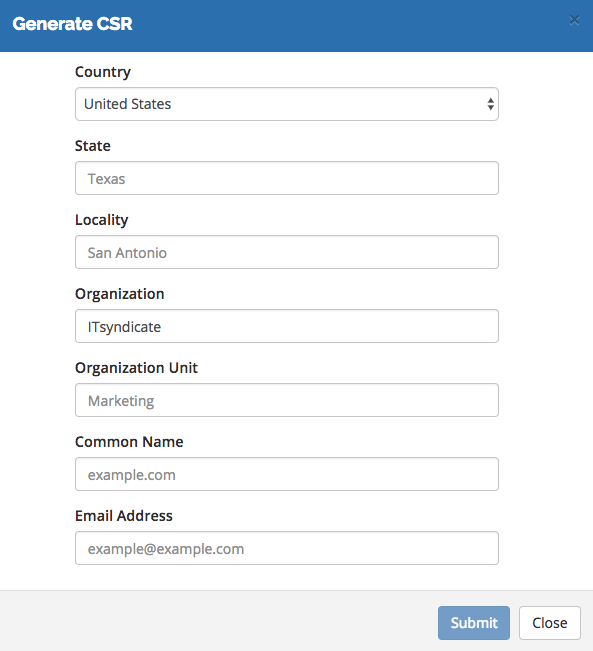
As soon as you completed CSR generation you can move to the administrative contact of the SSL certificate and click the Continue button.
When you're requested to select the Certificate Approval option I recommend you to use the HTTP option.
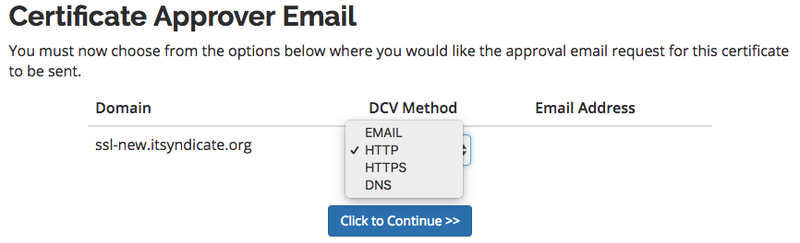
This option allows you to put a file to your server to approve your domain. This option is like the Google Webmaster domain verification method, and everyone who is familiar with this option will do it without any issues. Then click the Continue button and back to Service Details.
As a result, on the Service Details page, you will see information about the file you should upload to the server.
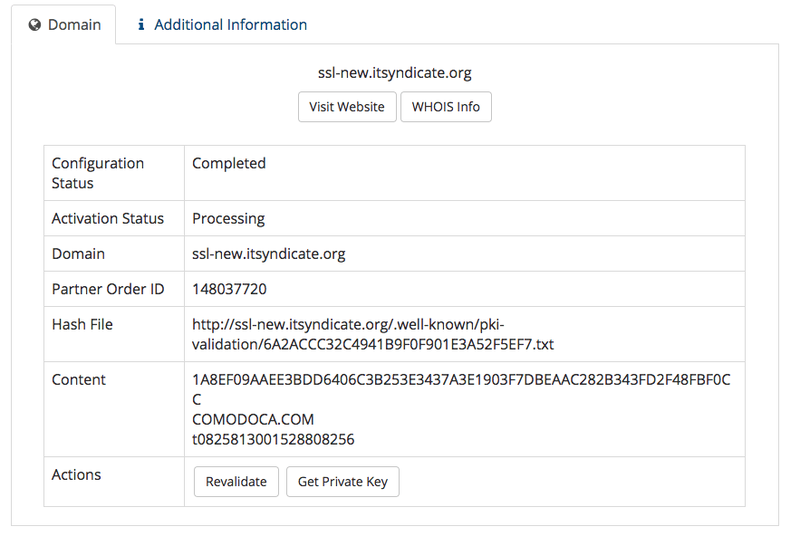
Now you need to create a directory in your web server root `.well-known/pki-validation`, you can do that via FTP server or with bash command:
mkdir -p .well-known/pki-validation
Put your validation file from the Hash File field with content from the Content field to the server via FTP or with bash command:
nano .well-known/pki-validation/{YOUR_VALIDATION_FILE}.txt
and press the Revalidate button. As soon as you get a Success message you will receive a zip archive to your Administrative contact email. Now you are ready to install your new SSL certificate to your EC2 instance or Linux server.
To install an SSL certificate on your EC2 instance you need to SSH to your instance and configure the webserver to serve secured connections.
For your comfort create a directory for each domain that will have SSL certificate:
mkdir -p /etc/nginx/ssl/live/YOUR_DOMAIN
NB! Do not forget to change YOUR_DOMAIN to your real domain name.
Put your private key to /etc/nginx/ssl/live/YOUR_DOMAIN/privkey.pem , and your SSL chain to /etc/nginx/ssl/live/YOUR_DOMAIN/fullchain.pem
To make a full chain go to Client Area, select your SSL certificate, and copy-paste Certificate (CRT) and Intermediate/Chain files to fullchain.pem
Finally, it is time to configure Nginx vhost file to server SSL connections on your EC2 instance. Here is my example:
server {
listen 80;
server_name ssl-new.itsyndicate.org www.ssl-new.itsyndicate.org;
}
server {
server_name www.ssl-new.itsyndicate.org;
listen 443 SSL;
expires 1y;
ssl on;
ssl_stapling on;
ssl_certificate /etc/nginx/ssl/live/ssl-new.itsyndicate.org/fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/live/ssl-new.itsyndicate.org/privkey.pem;
ssl_session_timeout 24h;
ssl_session_cache shared:SSL:50m;
ssl_dhparam /etc/ssl/dhparam.pem;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA';
return 301 https://ssl-new.itsyndicate.org$request_uri;return 301 https://ssl-new.itsyndicate.org$request_uri;
}
server {
server_name ssl-new.itsyndicate.org;
listen 443 SSL;
expires 1y;
ssl on;
ssl_stapling on;
ssl_certificate /etc/nginx/ssl/live/ssl-new.itsyndicate.org/fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/live/ssl-new.itsyndicate.org/privkey.pem;
ssl_session_timeout 24h; ssl_session_cache shared:SSL:50m;
ssl_dhparam /etc/ssl/dhparam.pem;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA';
root /var/www/ssl-new.itsyndicate.org/public_html;
access_log /var/log/nginx/ssl-new.itsyndicate.org-access.log;
error_log /var/log/nginx/ssl-new.itsyndicate.org-error.log;
try_files $uri/index.html $uri.html $uri/ $uri =404;
index index.html;
error_page 404 /404.html;
}
After configuration is done test and reload Nginx web server so the changes take effect:
nginx -tservice nginx reload
Hence it is time to check that your EC2 SSL instance works correctly. Open your browser and enter your domain into the search bar. If everything is OK you should see a valid SSL certificate.
Renew SSL certificate
The process of renewing an SSL certificate is almost the same as ordering a new SSL certificate, but you should select "Renewal" as the order type. You may start renewal within 90-days before expiration after the renewal process is done your certificate will be added to the old one and remained days will be also added. Also, you should use your old CRS in order not to change the private key. In case you lost it, you can always generate a new one, but in this case, do not forget to change Private key.
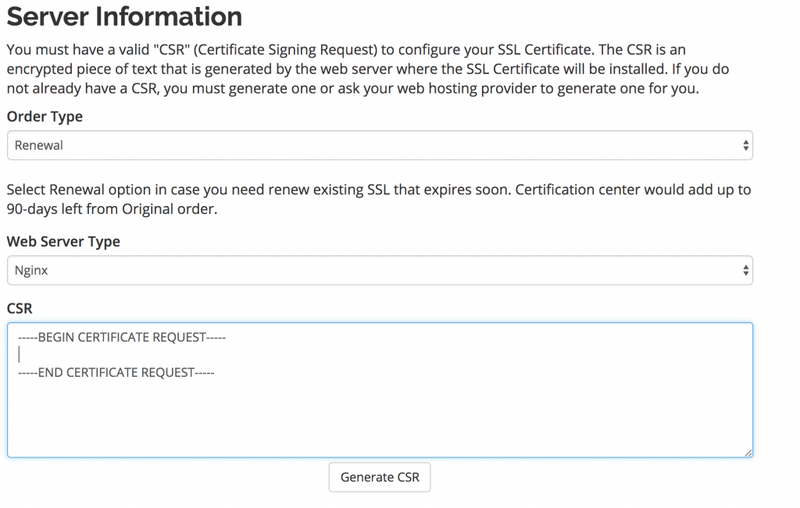
Above all, you should keep in mind that renew SSL certificate is not the same process as domain name renewal. Because you should upload the new version of the SSL certificate to the server. Therefore repeat step 2 to install new version of SSL certificate to your Linux server.
Conclusion
Now you know how to install a new certificate on AWS EC2 instance or any Linux server. Please pay attention not to forget to renew SSL certificate when the time comes. With our proactive server management services, you should not worry about renewing SSL certificates, as our monitoring system checks SSL certificates and reports any issues to our technical team. As soon as we get an alert we start an upgrade process and notify our clients. This is a good option not to care about the SSL certificate and its expiration and just know that it works!
Don't know which certificate is right for you?Contact us!
Docker commands and Dockerfile usage for running containers on a local machine
Docker commands and Dockerfile usage for running containers on a local machine
Netflix tech stack for powering streaming backend and cloud solutions





