Crafting cutting-edge VPN infrastructure: ITSyndicate's journey and expertise
Choosing the right cloud provider: the first step to excellence
As the seasoned cloud engineering team at ITSyndicate, we've successfully crafted numerous VPN infrastructures for our esteemed clients over the years. This piece seeks to provide insights into our VPN infrastructure-building journey, the challenges we encountered, and our strategies to tackle them. The initial step in this process is opting for a suitable cloud provider. We've worked with various providers, such as Amazon Web Services (AWS), Google Cloud Platform (GCP), and DigitalOcean, each presenting unique services that enhance VPN infrastructure building, including virtual private clouds, load balancers, and firewall rules. In this case, we chose DigitalOcean as the central location of our infrastructure and many other less familiar providers to provide customers with access to the Internet from various parts of the world.
Designing the architecture: balancing needs and performance
The next phase involves designing the VPN infrastructure's architecture after selecting a cloud provider. This action consists in recognizing the resources required for the VPN application, encompassing servers, storage, and networking resources, always with an eye toward scalability, reliability, and security. Upon completion of this phase, we possessed a robust project plan and diagram that served as the foundation for the subsequent set-up process.
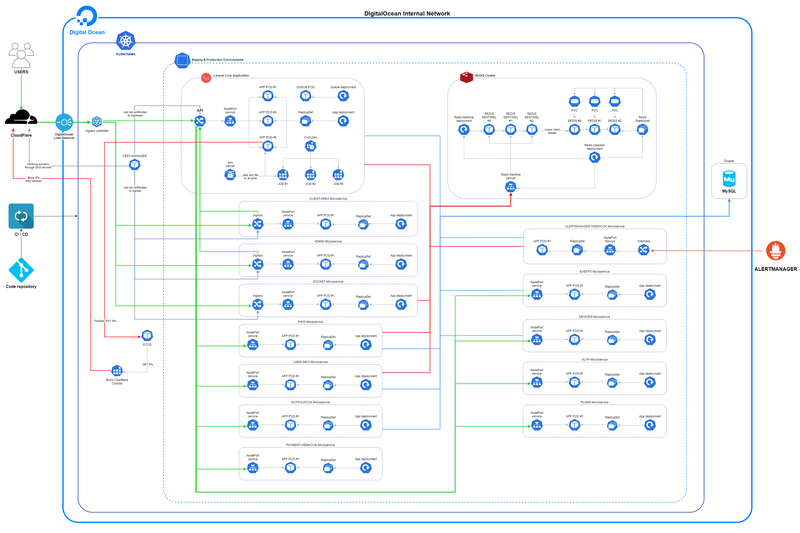
Database and caching: powering performance and reliability
While focusing on servers and networking resources, we also address the database and caching demands of the VPN application. Often for such projects, we use MySQL as our database and Redis for caching, significantly enhancing the performance and reliability of the VPN infrastructure.
Harnessing the power of Kubernetes
Kubernetes, a powerful container orchestration platform, is a frequent ally in this phase. It enables us to efficiently manage and deploy containers at scale, ensuring high availability for VPN servers and databases and facilitating scalability as per demand.
VPN server setup and software configuration: the heart of infrastructure
Having designed the infrastructure, we focus on setting up VPN proxy servers and configuring the VPN software. This point typically includes installing and configuring VPN server software such as OpenVPN or StrongSwan and configuring firewall rules to permit incoming VPN traffic while safeguarding server security.
Overcoming challenges: the road to success
Occasionally, we encounter challenges like configuring firewall rules or ensuring proper VPN server setup for supporting the VPN software. We navigate these by meticulous configuration review and troubleshooting to guarantee a flawless VPN infrastructure setup.
Ensuring peak performance with rigorous testing
We focus on thorough testing once the VPN infrastructure is configured and set up. This part includes connectivity, performance, and security assessments to certify that the VPN infrastructure delivers reliable and secure service.
Embracing continuous integration with GitLab
GitLab, a remarkable tool, has often been integral to this phase. We use it to implement a continuous integration and continuous delivery (CI/CD) pipeline for the project. It enables swift and seamless deployment of updates and modifications to the VPN servers, ensuring they operate on the latest version of the VPN software.
Enhancing Security and Performance with Cloudflare Cloudflare, a widely adopted cloud-based service, often complements our VPN infrastructure-building efforts. It shields the VPN infrastructure from threats like DDoS attacks while enhancing VPN server performance.
Reliable monitoring: a step towards smooth functioning
Post-launch, our focus remains on vigilant monitoring to ensure smooth operations. We monitor servers, databases, and caches for performance and availability and keep an eye on VPN traffic to pre-empt potential issues.
Endnote: the expertise and dedication of ITSyndicate
Crafting a reliable, secure infrastructure for VPN applications demands meticulous planning and attention to detail. At ITSyndicate, our cloud engineers boast the expertise and experience to prepare a robust VPN infrastructure tailored to our client's needs. We've skillfully leveraged a range of tools and techniques, including Kubernetes, MySQL, Redis, GitLab, and Cloudflare, to construct VPN infrastructures that are reliable, secure, and scalable.
If you're considering building a VPN application and require a robust infrastructure, ITSyndicate is your trusted partner. We guide you through the entire process, from choosing a cloud provider to crafting the architecture, setting up servers, and configuring the software. With our experience and proven track record, we're confident of delivering a VPN infrastructure that meets and exceeds your expectations.
Reach out to us today to discover more about our services and how we can assist in creating a reliable and secure VPN infrastructure. We're committed to delivering outstanding results and are eager to help you architect a VPN infrastructure that satisfies your client's needs.
Docker commands and Dockerfile usage for running containers on a local machine
Docker commands and Dockerfile usage for running containers on a local machine
Netflix tech stack for powering streaming backend and cloud solutions





