Nowadays the Internet is full of things and people that want to use the results of somebody’s work for their own profit. Modern website and e-commerce business owners face problems with hacking attempts (both successful and not), data theft, money robbery, and even usage of their server and website as a base for crypto-mining software working on the background. The cases are really various and in most of them malware hides itself. It starts to be notable when the results and the harm done by it begin to cause significant problems. They usually begin affecting on the end user’s impressions. So how to secure website and server and be sure that performed actions have a real effect? To answer that question we need to start from the very beginning. We need to review why hacking attempts are possible and what doors we leave open that allows hackers and attackers to come inside.
What are the reasons of hacks and malware integrations?
Outdated versions of software and application
85% of the hacks done today are caused by open vulnerabilities in outdated versions of the software and application. You’ll laugh, but that’s also one of the easiest ways to break through. Why? Cause all such vulnerabilities are public and are posted for everyone. Why do you think developers of various products and tools we use, constantly deliver newer and newer patches and modifications? Because hackers never sleep…)
Breaking through such vulnerabilities is pretty straightforward: all you need to have is simple bot (it’s software application that runs automated tasks or scripts over the Internet), configured in a way to go through all known backdoors and try to upload or do something. You don’t need to perform some kind of cunning actions, like it’s shown in movies.)
Zero-day vulnerability
What’s that? It’s an exposure, which is unknown to all parties, that are responsible for the product and who are interested in its further patching, upgrading, etc. These parties usually are:
- Team, responsible for project maintenance
- End users
So as a conclusion - zero-day vulnerability is a backdoor no one is aware of. It’s just there, like a hole covered with a small rug. No one knows about it, cause no one has put their feet there and felt the pain of crush.
Breaking through it is not as easy as it is with outdated software, as such fragility is usually hidden from everyone. But when it’s located by someone with bad intentions - the only thing left is to wait and feel the consequences.
However attackers are loving zero-day vulnerabilities ‘cause, there is still no security patch to stop them (at least for now), and the only thing that may block them is the level of exploitability the exposure allows.
Suspicious plugins and extensions
Many current Content Management Systems (CMS) allow expanding their functionality by adding plugins. The biggest quantity of plugins are developed for WordPress, Magento, OpenCart, etc. The tricky thing here is that these extensions are also one of the biggest vulnerabilities or even malware sources that may harm your website, application, or even the whole business.
What is the plugin itself? It’s some additional code, designed as a separate service, that allows you to expand some core functionalities of the website or just add another feature to it. Where are they downloaded from? In most cases, they’re found by website owners somewhere in the Net or just with the first Google link that forwards them to GitHub.
The thing that is not considered here is that every piece of code added to your system has the potential to be a risk. When you download some kind of plugin from the Internet and set it up on your website without being aware of what’s inside it and who is the author - all you do is granting that potentially risky or even malware code full access to your website and its data. So if the plugin has a vulnerability (and in the majority of the cases we face it’s just like that) or is not a plugin at all (meaning that it’s just wrapping for the malware) consider that your website and data are already penetrated.
Bad code
As well as the plugins: every piece of code added to your system has the potential to be a risk. That’s why in professional and qualitative development companies there is a separate Quality Assurance (QA) department and Vulnerability Researchers (VR) department. Both of them are constantly looking for potential exposures and bugs that may cause such exposures to appear.
How to secure website and server properly?
Actually, I think it’s enough to talk about how hackers can compromise and hack your websites. I think it’s time to tell you how to secure server and website backdoors and prevent hackers and malware from gaining access to your system.
WAF
Web Application Firewall (WAF) is a tool for filtering, monitoring, and blocking HTTP / HTTPS traffic to and from a web application. In simple words that’s a pretty dumb tool, that allows cycling the traffic through certain rules configured inside it. WAF passes the traffic further if it doesn’t violate any of the specified rules and blocks it immediately if it does.
Although you need to acknowledge the fact that WAFs are not perfect and can be bypassed when for example a zero-day vulnerability exploits an attack vector that is not yet handled by any of the WAF’s rules.
Update it & don’t let it be default!
As we said above one of the most spread and easy backdoors is outdated software. It is incredibly important to keep your website updated as soon as a new plugin or CMS version is available. We mentioned above that bots can easily detect vulnerabilities. What we didn’t mention as besides that such bots can crawl the whole Net and detect the sites with outdated software and open exposures and then get their bad and dirty hands in it.
The default settings of basically all CMS’s are a mess. For example, some CMS allows to setup of any kind of extensions to any kind of user. So one day you just come by to check on your business and see that some user installed some extension and it deleted all your data. Don’t let it come to that, review the security settings of the CMS carefully before going live, as it’s just worth it. If you're not sure that your security barriers are good enough, you should look for some qualified service provider. It will review your security settings and consult you on how to secure website and server for maximum protection.
Extensions / plugins selection
So how do you know which plugin is bad and which one is good? The first thing you should look at is the frequency of updates for this plugin. If the author released last update around 1 year ago - then you should suspect something bad. Probably the author has already stopped working on that extension and there won’t be any further updates as well as security updates, right? You need to understand that in most of the cases plugin’s actions are tied up with the business logic of your website. So what’s the point of installing potentially risky functionality to your website, that won’t only be a backdoor for hackers, but also can become a problem for the business in total?
Also, you should look at the author of the plugin. The larger the user base, the more extensions, and the better rating author have the less likely his / her extensions will damage your business and their reputation by inserting malicious code. And less likely hackers will try to break in into plugins developed by experienced authors, as invest/profit variable for them will be too low.
Passwords
`admin/admin`, really?!) Sometimes hackers don’t need to think about something outstanding to break through, as website owners just leave the door open for them. By following this link you can see the list of the most common passwords used in 2022, and if yours is among them - then you should change it. I mean, right now. Right, this second!
The guys in WP Engine did awesome research regarding myths surrounding passwords. It’s awesome, check it out!
There is a golden rule for passwords - CLU:
- C for Complex
Your favorite sports team or birth date is definitely a bad idea! Hackers can find all that information on any social page you have, so using that as a password for your personal and business-sensitive data is definitely not a good idea.) Try to generate complex passwords that consist of various letters, numbers, and additional symbols.
- L for Long
Try to use passwords that are up to 12 characters long. Most of the modern online login systems limit the number of unsuccessful login attempts, so breaking through will cause a problem with a 12- and more characters password, as most of the crack algorithms are based on simple permutation.
- U for Unique
Yes, that’s right, the best and the most secure way is to have a unique password for each service. So having one password for everything means having a single point of failure for everything, as getting access to a single service means getting access to your whole e-world.
- V for Vendetta
Oops, not the right place for that...) The movie is great though.)
You may ask: "How to store all that? I can’t remember all long and unique passwords!" Well, in the modern world there is a huge bunch of various tools designed for safe storage of your passwords and logins. We use offline KeePass for that and there is a better-looking version of this app called KeeWeb.
Users permissions and accesses
Having strict policy for on-site users’ privileges and accesses will low the chance of hacks and intrusions by `rogue` user accounts. Do not allow multiple access for 1 account and configure logging for all users actions in order to track changes and actions of the users. We’re not saying about tracking each click of the user and looking from behind of his back to steal his credit card data, we’re talking about tracking their actions on the website, so you easily spot unusual behavior, catch anomalies and confirm with the person that no one has compromised their account.
Secured server
Security is a complex term, consisting of different aspects and security layers. Each of them cuts and filters certain data and activities.
One of them is server security which should work in full cooperation and coordination with the code. Here we’re talking about:
- separating php-pools for each website running on the server
- adjusting directory and files permissions
- setting up intrusion prevention tool
- disabling directories listing
- etc.
External backups
What should you do if everything is gone? Of course, many modern website owners know pretty much about backups and they know it’s really important. The only thing they don’t consider is that keeping backups on the same server is not a good idea at all.
Why? That’s one of the main security risks, as backups kept on the web-server always contain some old and unpatched versions of your CMS and extensions which are publicly available. So hackers receive an easy way to access your server along with all its data. In our opinion, the best way to keep your backups will be to use some external storage or even an external backup service. Besides security risks, backups stored on the same hardware with your website are kinda useless, as:
- If hardware fails, it will fail with all backups and you won’t have a way to restore your site
- If a hacker comes in, he receives access to everything. And then an attacker can easily infect or delete the backup copies as well as the live site. The rest is history…)
Security solution by ITsyndicate
The things highlighted above are basic and are common for the majority of cases. But don’t consider the above as a full list of actions that will cover all possible exposures of your server. Ignoring basic application-side security approaches described a few paragraphs above, like basic updates of the plugins and software, leads to nothing but repeats of the hacks or intrusions.
We’ve already told you enough about the possible methods to break into the server and described how you can deal with it. If you think that your website or server is not secured or you’ve already noticed some suspicious activity, then you should definitely think about the above security measures.
Experienced and technically-savvy website owners, developers, and system administrators can cover most of the specified above. But what should you do if you don’t have a clear understanding of what, where, and how? Well, we’re glad to announce a little upgrade of our services, as now ITsyndicate begins to provide website and server security hardening as well as website malware cleanup.
So now we come to a topic named...
How it works
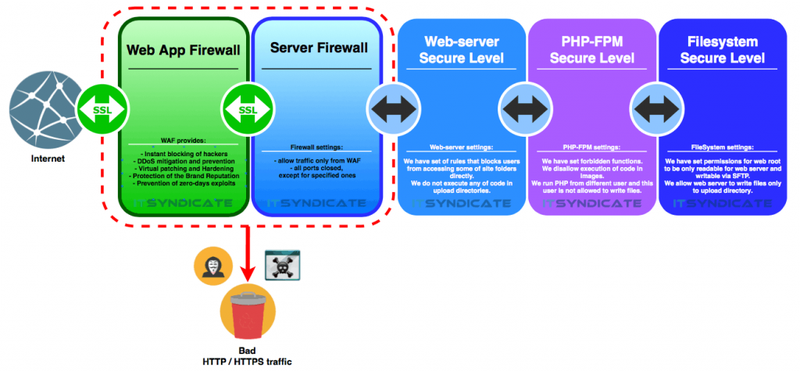
The above security schema shows how we’ll configure security layers for your web-server. The idea of such layering works and has proven itself in various cases. So let’s start from the beginning:
WAF
which takes the first bullet in such a setup and does a majority of dirty work like:
- instant blocking of the hackers
- DDoS attacks mitigation and prevention
- virtual patching and hardening
- prevention of zero-day exploits
In addition to above, this layer is constantly improved, as research is done every day enhances detection and further mitigation of evolving threats. Besides that you can configure a set of your own custom firewall rules on this level, to be sure that they covered your application’s bottlenecks and potential backdoors (if you’re aware of them).
After traffic has passed WAF security level and the firewall filtered it from all suspicious, bad, and unknown requests it goes to…
Server firewall
What’s the point? First of all server firewall will only let through the traffic which WAF has already checked. So if some kind of handyman finds a way to get around WAF he/she won’t be able to go further as the server firewall won’t pass it. So main features of server firewall are:
- allow traffic only from WAF
- allow traffic to go only through specified ports (custom configured for each case)
We forgot to mention SSL certificate, right? No, we didn’t!) Keep in mind that SSL doesn’t do anything to protect the site or server against any kind of attacks, or stop it from distributing malware. SSL certificate encrypts the data sent from Point A to Point B (for example web-browser and web-server). What for? Encryption prevents anyone from being able to fit into the chain and steal the data sent from A to B. Such an attack's name is Man in the Middle. Also, Google has begun to force all website owners to move from regular and old HTTP to HTTPS, you can read more about it in one of our previous blog posts.
After traffic went through the first two security layers it comes to server-side security tiers. Our team handles their configuration from scratch. The first one here is…
Web-server security layer
where we configure a set of rules that blocks users from accessing some of the site’s folders directly. Also, we restrict any kind of code execution in upload directories. Then it comes to…
PHP FastCGI Process Manager security layer
which in its turn has:
- a set of forbidden functions, execution of which will be blocked
- block execution of the code inside of images
- a rule to run PHP processes from different users with disabled permission to perform WRITE operations to the files
And last but not least…
FileSystem security layer
where we set:
- permissions for web root folder, so it’s only READable for web-server and WRITable for sFTP
- WRITE operation for users is allowed only to /uploads directory.
Security service features
Furthermore, we’re constantly monitoring your website for the presence of various vulnerabilities, signs of website hacks, intrusions, and also warnings from blacklist authorities. If we see anything suspicious going on - we’ll contact you right away to indicate and begin resolving the issue. Besides that, the above security solution will detect downtime and changes of your DNS settings, core file integrity, and SSL certificates and we’ll alert you if we find anything suspicious. Below you can see the full list of malware and security issues that ITsyndicate detects and resolves with the help of the security solutions we provide:
- Notorious website hacks
- Issues and anomalies with the web-server and website security
- Warnings from blacklist authorities
- SSL Certificate changes
- SQL injections
- DNS Record Changes
- Core file totality
- Spam injections from Blackhat SEO
- Malicious redirects inserted into the JYJcode / configs
- Dirty search engine results
- Hidden and malicious iFrames
- Mobile malware infections
- Phishing lures
- Hijacked Websites
- Obfuscated JavaScript injections
- Redirects targeting mobiles
- Drive-by-Download injections
- Email spam abuse
- Pharma hacks
- Desktop AntiVirus Blacklisting (i.e., AVG, Norton, McAfee)
- Infected database / SQL Injections
- Website defacements
- Embedded trojans
- Cross-Site scripting - XSS Infections
- Search engine blacklisting (Google, Bing, Yahoo, etc)
If you’d like to know more about us, and our services or just get in touch to know if we like playing ping pong or not - feel free to contact us via [email protected] ! We’ll be glad to talk and tell you about our best practice approaches and experience!
Docker commands and Dockerfile usage for running containers on a local machine
Docker commands and Dockerfile usage for running containers on a local machine
Netflix tech stack for powering streaming backend and cloud solutions





